Exceptions = Compromise.... Trust Nothing, Verify Everything
Gain instant clarity into what’s happening across your endpoints, applications, and network, so you can act faster and defend better.

MZT’s Cyber Insights engine surfaces real-time context, audit trails, and system intelligence in one place. Helping IT and security teams make decisions with speed and confidence.
Track every action taken by applications, users, and devices across your environment in a searchable, timestamped log.
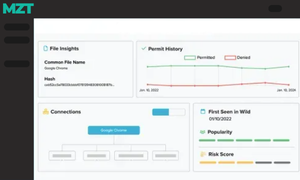
Get a full scope of the application request as well as comparison across millions of endpoints. Make an informed educated decision - not a guess.
.png)
View clear visual timelines showing process relationships, parent-child execution paths, and behavioral context.
Monitor and review every executed script or CLI command, even those run by trusted apps like PowerShell or cmd.
See which applications are reaching out to what IP addresses and ports. Identify unauthorized connections instantly.
Track system-level modifications in real time to identify tampering, misconfigurations, or persistence techniques.
Insights bridge the gap between data and decisions. When you know what’s running, who launched it, and what it tried to do. Stop reacting blindly and start responding with purpose.
With clear, real-time context, your team can triage and remediate faster — without digging through raw logs.
Use behavioral intelligence to refine allowlisting and Ringfencing rules based on real usage, not guesswork.

Because what you can’t see is what puts you at risk.
Insights is just a part of the entire security suite. Learn about other features that can better your security.
Prevent unauthorized software from executing with default-deny policies and precise control over what’s allowed to run.

Contain approved applications and control what files, scripts, and resources they can touch; even after they launch.
Block data exfiltration through USB drives, cloud sync tools, and unapproved storage paths with location and user-based rules.
Grant just-in-time admin privileges without compromising endpoint security or giving away full control to users.
Cyber Insights is MZT’s visibility engine that collects, correlates, and presents endpoint activity in a human-readable format to support security decisions.
By only having the insights you only have the data but no action. MZT aims to provide proactive controls to better the security of your enviorments.
Data retention is configurable, with options to keep logs for up to 365 days for some account types.
Unlike legacy tools that rely on detection alone, MZT prevents unapproved actions by default, greatly reducing the attack surface. MZT also has the in house support team to support you as well at no additional cost.
Yes. MZT includes multi-tenant management, role-based access, and policy templating; ideal for MSPs and MSSPs.
Yes. MZT is fully cloud-managed, allowing centralized control, remote deployment, and real-time updates from anywhere.
No. MZT is built for MSPs, MSSPs, and mid-market companies as well as large enterprises. It's scalable to any size and security maturity level.
Deployment depends on the method in which we are able to push out the agent. Could be as fast as a few hours if done through a common preferred method.
Yes. MZT complements antivirus, EDR, and other tools to enforce Zero Trust policies. It does not require uninstalling existing solutions.